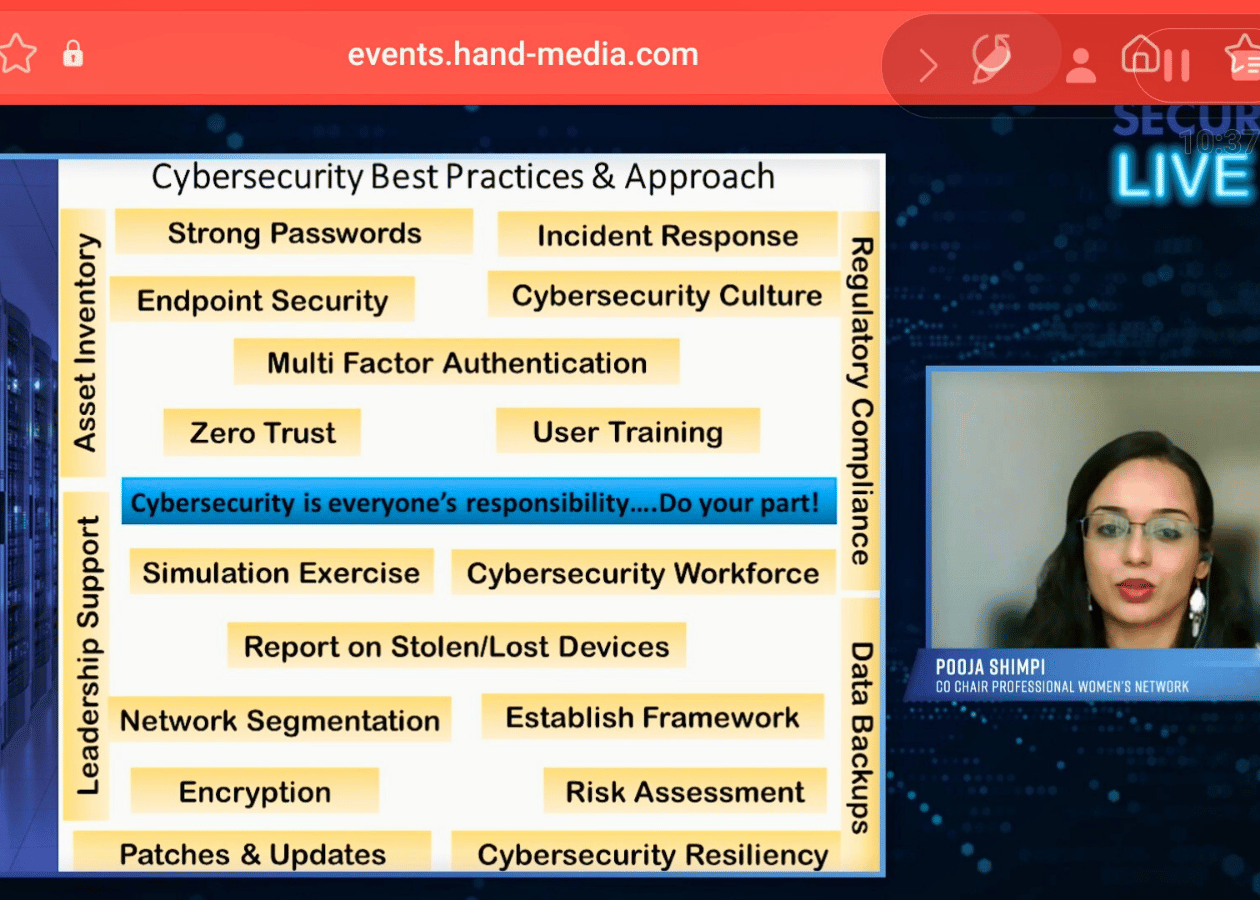
Taking the Stage: My Security Buyer Live Journey as Headline Speaker
There’s a unique energy that comes with being selected as a headline speaker at Security Buyer Live a recognition that your insights matter, your experience resonates, and your voice can guide fellow security professionals navigating our industry’s most pressing challenges. My session focused on what keeps every CISO awake at night: evolving threats, resilient response strategies, and the persistent skills gap threatening our collective security.
Why Modern Cybersecurity Demands a New Paradigm
The world I addressed at Security Buyer Live was navigating through unprecedented global disruptions. Security professionals had been forced to rapidly reprioritize their approaches to cyber and information security, often with limited resources and mounting pressure.
It became increasingly clear that adaptation wasn’t temporary—it was the new normal. Organizations faced:
My expertise spans critical security domains:
Policy and framework development aligned with NIST and ISO 27001/27002 standards
Regulatory compliance management in heavily regulated financial environments
Cybersecurity education and awareness programs that actually change behavior
Risk and incident management when theory meets crisis reality
Data governance and identity access management protecting sensitive information
Audit preparation and remediation satisfying both internal and external scrutiny
This comprehensive GRC background allowed me to address security challenges holistically understanding that technical controls, governance frameworks, risk management, and compliance requirements must work together seamlessly.
The Top Cybersecurity Challenges I Highlighted
My presentation identified the threats keeping security leaders vigilant:
Ransomware attacks on critical infrastructure: No longer just opportunistic crimes, these attacks target essential services with devastating potential. The threat wasn’t going away—it was growing exponentially.
Supply chain attacks: Adversaries recognized that compromising one vendor could breach hundreds of organizations. The interconnected nature of modern business made supply chain security everyone’s problem.
Deepfakes: Emerging threat vectors using AI to impersonate executives, manipulate media, and enable sophisticated social engineering at scale.
Zero-day vulnerabilities: Unknown flaws being exploited before patches exist, requiring defense-in-depth strategies that assume compromise.
Skilled workforce shortage: Perhaps the most critical challenge millions of unfilled cybersecurity positions globally while threats accelerate.
Financial Services in APAC: Unique Regional Insights
My role in the financial services industry across APAC provided unique perspective on regional trends:
Cloud-based attack risks: As organizations migrated infrastructure to the cloud, attackers followed. Secure configuration wasn’t optional—it was existential.
Regulatory compliance intensity: APAC regulators were placing unprecedented emphasis on cybersecurity compliance as attacks made headlines. Organizations needed frameworks that satisfied multiple jurisdictions simultaneously.
Social engineering and user education: I shared real examples, including a Singapore bank where customers lost millions to phishing scams via SMS impersonation. The most sophisticated technical defenses fail when humans are the target.
The Critical Role of Information Sharing
One of my key messages emphasized that cybersecurity is a collective challenge requiring collaborative response. Adversaries share information, techniques, and tools freely. Defenders must do the same.
When peers from similar sectors proactively share threat intelligence and collaborate on defenses, everyone’s resilience strengthens. However, this requires:
Trust between organizations that might otherwise compete
Structured approaches to what, when, how, and why information is shared
Cultural commitment to viewing cybersecurity as shared responsibility
Active collaboration that reduces collective risk
As I told the audience: “Understanding these building blocks can help develop structures that not only build trust but also actively support collaboration in reducing cybersecurity risks.”
Addressing the Skills Gap Through Mentorship
I concluded by addressing perhaps our industry’s most solvable challenge: the skills gap. With proper guidance, we can significantly increase the cyber workforce.
This conviction led me to found “Protégé for Women in Cybersecurity”, showcasing inspirational stories of mentors and mentees, and later to lead the Global Mentorship Program for Cyber Riskers community—free and open to everyone.
My vision is simple but powerful: provide support to those who need it most—young enthusiasts, women returning after career gaps, career changers. Because it’s not who you are or where you come from, but what you can and will do that defines you.
Why Equality Elevates the Entire Industry
When asked about equality in cybersecurity, my response was direct: Diversity in any field results in higher productivity and better outcomes. Women represent over half the world’s population yet comprise only 20-25% of the cybersecurity workforce.
This isn’t just an equity issue it’s a strategic vulnerability. Women bring unique perspectives to risk assessment, problem-solving, and security design. The industry’s capability and unlimited scope for growth depend on attracting and retaining diverse talent.
The Purpose That Drives Us
I distilled the purpose of information security professionals into one sentence:
“To protect and secure organizations against the constantly evolving security threat landscape, learn and keep up with the pace, and improve the organization’s overall security posture.”
This mission requires technical expertise, business acumen, regulatory knowledge, communication skills, and relentless adaptation—exactly why diverse teams outperform homogeneous ones.
Beyond the Webinar: Lasting Impact
Security Buyer Live provided more than a speaking platform—it created connections with security professionals facing similar challenges across industries and geographies. The interview for their magazine extended the conversation, allowing deeper exploration of GRC frameworks, ISO standards implementation, and practical approaches to building security cultures.
Being selected as a headline speaker validated years of work building expertise across information security domains, but more importantly, it created opportunity to guide others navigating these complex challenges.
The Continuous Journey
The threats I discussed at Security Buyer Live haven’t diminished—ransomware continues evolving, supply chains remain vulnerable, and the skills gap persists. But so does our collective determination to defend digital infrastructure, protect people’s data, and build resilient organizations.
Every speaking engagement, every mentorship conversation, every framework implemented contributes to strengthening our collective security posture. The work continues, and I’m grateful for platforms like Security Buyer Live that elevate important conversations and connect professionals committed to making our digital world safer.
Need guidance on implementing ISO 27001/27002 frameworks, strengthening GRC programs, or building effective security awareness initiatives? Let’s connect and explore how comprehensive security governance can protect your organization.
By – Pooja Shimpi | Cybersecurity GRC Professional & AI Governance Advisor